[ad_1]

Earlier than we will outline and map out the distinctive options of threshold cryptography, it’s obligatory to begin with a definition of cryptography itself. Cryptography is a course of for offering safety for info as it’s handed between two events, maintaining it safe from any third celebration adversaries or most people. The necessity for safety can come from varied apects – confidentiality, integrity or authenticity to provide some examples. Within the digital realm, this takes the type of writing, in addition to fixing, codes. Encryption is popping intelligible info into unintelligible info, and decryption includes deciphering the unintelligible info again into its authentic, intelligible kind.
In at the moment’s context, when individuals point out cryptography, they’re sometimes referring to cryptography as it’s utilized in laptop science – and more and more, to cryptocurrencies and decentralized monetary purposes.
It’s tough to pinpoint a exact origin for threshold cryptography or to attribute its invention to a single particular person. Whereas some individuals declare that the earliest publication of a system with full threshold properties was first published by Alfredo De Santis, Yvo Desmedt, Yair Frankel and Moti Yung in 1994, others declare that credit score ought to go to Adi Shamir and his article How to Share a Secret, revealed by MIT in 1979.
Early adopters of threshold cryptography have been restricted to the navy and governmental organizations. It wasn’t till 2012 that RSA Security released software that made threshold cryptography obtainable to the general public.
One of many earliest implementations was by a startup spun out of Bankers Belief within the Nineties, and it was for the deliberate deployment of the unique Secure Electronic Transaction, a regular for securing bank card transactions over a community. Nonetheless, in October 2012, after plenty of massive public web site password ciphertext compromises, RSA Security introduced that it might launch software program to make the expertise obtainable to most people.

Threshold cryptography methods are outlined by their distribution of knowledge amongst a “cluster”, and that is what makes them very safe methodologies. Within the context of cryptographic laptop expertise, this cluster takes the type of plenty of fault-tolerant, impartial computer systems. Fault-tolerance refers back to the skill of an working system (e.g., a pc) to proceed functioning regardless of a software program or {hardware} failure.
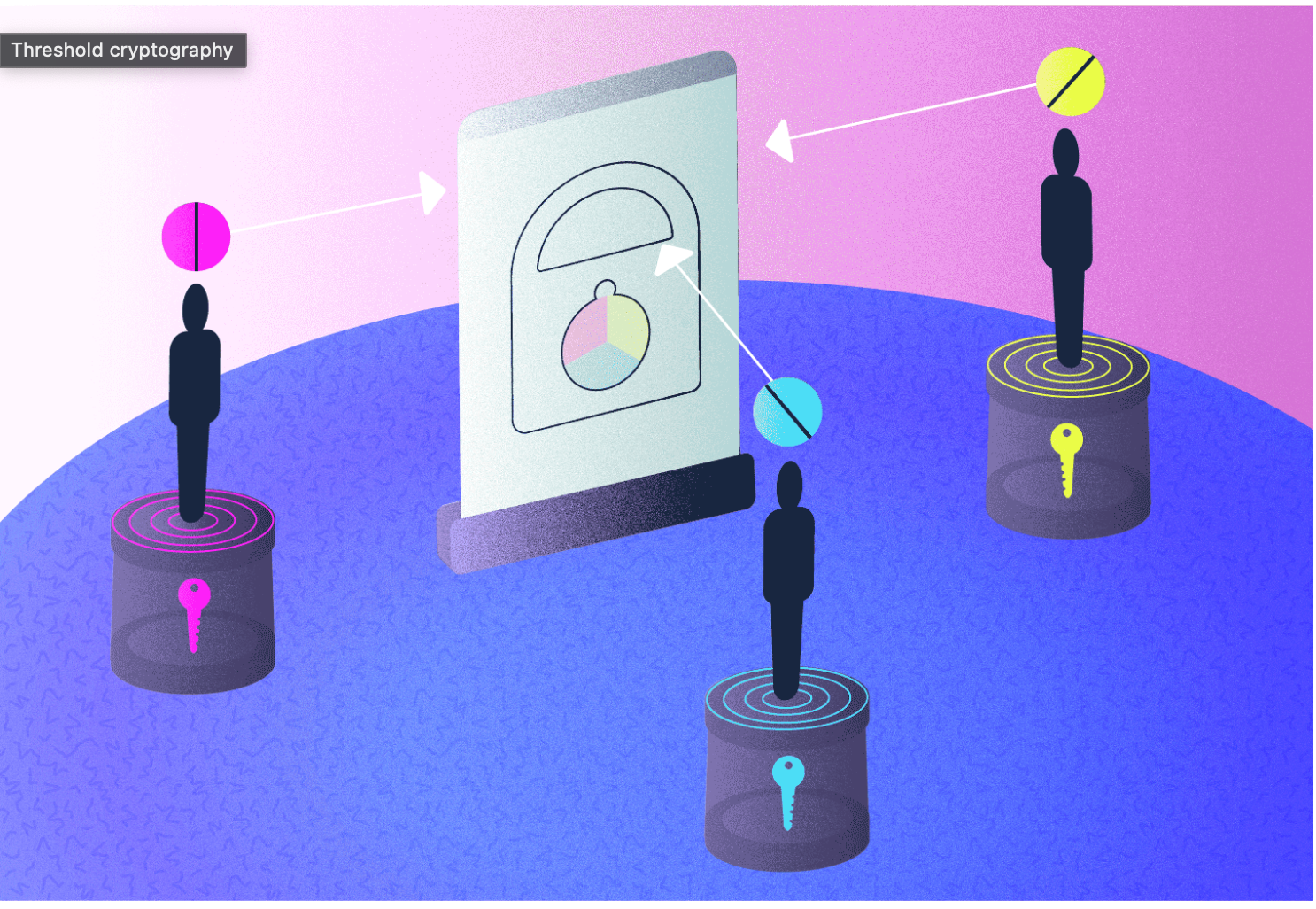
In fashionable cryptography, most methodologies have been developed to serve one sender and one receiver. The principle distinction of threshold cryptography, in addition to the principle motivation for its improvement, was to supply methods for situations with a number of recipients or a number of senders. Like all cryptographic methods, a message encrypted by means of a threshold cryptosystem makes use of a public key and a private key. Nonetheless, inside a threshold system the non-public secret is shared among the many particular person, impartial members throughout the cluster.
For instance, within the context of a threshold decryption cryptosystem, in an effort to decrypt any encrypted message, a predetermined variety of cluster members (i.e., the “threshold”) should all take part by executing the decryption protocol. Usually, the brink quantity is about up in order to mirror a majority of a given cluster. For instance, a cluster of 10 could have the brink set at 7, that means {that a} minimal of seven cluster members might want to cooperate for a decryption to achieve success. Collaboration doesn’t require that keyholders at any level see each other’s elements of the important thing; in actual fact threshold cryptography ensures that collaboration can happen whereas sustaining informational privateness.
Threshold cryptosystems are designed to keep up an authentic philosophical motivation behind cryptocurrencies – of eradicating trusted intermediaries, centralized entities and actors who’re “too-big-to-fail”.
Threshold cryptography gives the formal, structural mechanics for a lot of decentralized cryptographic applied sciences. Threshold cryptosystems permit customers to keep away from counting on a centralized authority or particular person to guard their knowledge or property, as that reliance could make a system extra weak, vulnerable to censorship, or corruption. Whereas threshold methods are definitely vulnerable to individuals performing in unhealthy religion (a number of cluster members, for instance, might try and collude with each other), to ensure that this collusion to be efficient, it must contain sufficient members to realize the brink. Nonetheless, if the brink is achieved, then it’s possible much less a matter of collusion than considered one of democracy – i.e., majority rule.
Threshold cryptography additionally ensures that the system is just not totally reliant on every single cluster member taking part. If a member both loses their non-public key info or is unable to take part within the protocol, this doesn’t deliver issues to a standstill. No single particular person has the power to create a bottleneck, both intentionally, or by means of likelihood. The truth that threshold cryptography doesn’t depend on full participation is a main instance of the system’s fault tolerance: there is no such thing as a single level of failure.
Threshold Network affords a full suite of decentralized providers constructed utilizing threshold cryptography, together with Threshold Access Control, Threshold USD, and the Bitcoin-to-Ethereum “bridge”, tBTC. Not solely does threshold cryptography inform the structure for all of Threshold Community’s Web3 purposes, it additionally informs the structure for governing the community itself. Threshold Community is managed by Threshold DAO (decentralized autonomous group), a neighborhood who collectively vote to determine on main points going through the community, in addition to updates to its governance course of. Anybody who holds Threshold work tokens (T) can take part in governance. Token holders also can run a node on the community and stake their tokens, thereby contributing to the performance and safety of Threshold’s purposes.
Future weblog posts will dive into varied elements of Threshold’s platform, however within the meantime listed here are some key weblog posts addressing varied elements of the protocol and its philosophical underpinnings:

[ad_2]


